cURL Error 60 SSL Certificate Problem: How to Fix
The "cURL error 60 SSL certificate problem" is a common SSL error that arises when attempting to establish an SSL connection with a server. This issue typically occurs when a website or application is communicating with an external server using an HTTP client, such as Guzzle HTTP client in PHP, and encounters difficulties with the SSL certificate verification process. The error can manifest when the client is trying to establish a secure connection over HTTPS or SSH protocols.
Complete error message is,
cURL error 60 SSL certificate problem: unable to get local issuer certificate
What is an SSL/TLS certificate?
SSL/TLS certificates play a major role in establishing secure and encrypted connections between clients and servers on the internet. The acronym SSL stands for Secure Sockets Layer, and TLS stands for Transport Layer Security. Both SSL and TLS are cryptographic protocols that ensure the confidentiality and integrity of data exchanged between systems.
In this context, when one system (System A) seeks to establish a connection with another system (System B), the SSL/TLS certificate becomes a crucial component in the initiation of a secure communication channel.
The fundamental purpose of an SSL/TLS certificate is to verify the identity of the server to the client and vice versa. In the connection process, when System A initiates a connection with System B, it requests System B to provide evidence of its identity.
This evidence is furnished in the form of an SSL/TLS certificate, which contains key information about the server, including its public key. The SSL/TLS certificate serves as a digital passport, asserting the authenticity of the server.
Upon receiving System B’s SSL/TLS certificate, System A undertakes a verification process to ensure the certificate’s validity. This validation includes checks on the certificate’s expiration, the integrity of its digital signature, and confirmation that it was issued by a trusted Certificate Authority (CA).
If the SSL/TLS certificate passes these verification steps, a secure connection is established between System A and System B.
In summary, SSL/TLS certificates act as trust anchors in the digital world, enabling secure and authenticated communication between systems. They form the basis for the encryption of data during transmission, safeguarding sensitive information from unauthorized access and ensuring the integrity of online interactions.
What is CA?
A Certificate Authority (CA) is a fundamental component in the digital security, playing a crucial role in validating and authenticating the identities of entities on the internet. In the context of SSL/TLS certificates, the CA acts as a trusted third party responsible for verifying the legitimacy of the entities seeking certificates. The primary function of a CA is to issue digital signatures for these certificates, affirming the association between a public key and the identity of the certificate holder.
For an SSL/TLS certificate to be considered valid, it must be signed by a trusted CA. The CA achieves this by using its own private key to generate a digital signature for the certificate. This signature serves as a stamp of approval, signifying that the information contained in the certificate, such as the public key and the identity of the certificate holder, has been verified and can be trusted.
Importantly, CA certificates, often referred to as “root certificates,” contain the public key of the CA itself. These root certificates are embedded within web browsers and other systems by default, establishing a chain of trust. When a user’s browser encounters an SSL/TLS certificate during an online interaction, it can verify the certificate’s authenticity by checking the digital signature against the public key within the embedded root certificate.
Furthermore, the CA scrutinizes the requester’s information before granting a signature, ensuring that the entity applying for the certificate is indeed who they claim to be. This stringent validation process enhances the overall security of the SSL/TLS ecosystem, instilling confidence in users that the encrypted connections they establish are with legitimate and trustworthy entities on the internet.
Establish a secure connection between two systems
Establishing a secure connection between two systems can be divided into two parts.
- Validate server
- Validate user/client
In the next few lines, we will see establishing a secure connection process using a client(browser) and a server(webserver)
Validate server
The server generates a public key and private key and requests CA to sign the certificate with the server’s public key inside it. Then, CA signs the certificate using CA’s private key and sends back the certificate to the server. The server sends a certificate to the browser(user).
Each browser has a certificate validation mechanism. Browsers validate the certificate that is sent by the server using the CA’s certificate.
Validate user/Client
The server request to validate the user himself and the browser generates a public key and private key based on that request. Then, the browser requests the CA sign certificate with bowser’s public key inside it. CA signs the certificate using CA’s private key and sends back the certificate to the browser.
The browser sends the certificate to the server when communication happens the first time. The server validates the certificate using the CA’s certificate. After building the trust, the browser sends an encrypted symmetric key using the server’s public to the server.
The server decrypts the data using the server’s private key and gets the symmetric key. Now both the user and server have the symmetric key. After the symmetric key exchange is happening, all future communications will happen using that symmetric key. All those components and processes are called PKI - public key infrastructure.
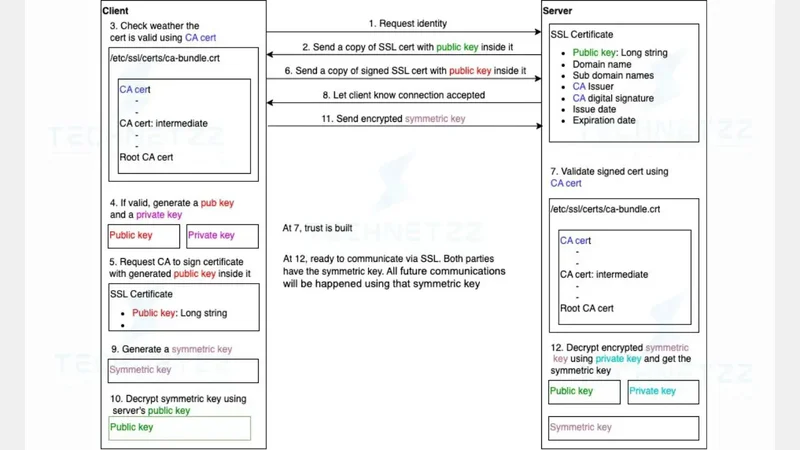 Establish a secure connection between a two systems
Establish a secure connection between a two systems
Resolve the “cURL error 60 SSL certificate problem”
To fix this error, download the certificate bundle and configure the php.ini file with proper configurations.
What is a bundle of CA root certificates?
The Mozilla NSS root certificate store issues this bundle of CA root certificates. The file contains certificates of public CA. Since all the certificates are in pem format, you can use them directly for SSL client authentication. Mozilla updates this file from time to time.
Some trusted and popular certificate authorities
Here I show you only a few certificate authorities. There are so many certificates available in the bundle from different certificate authorities. Please check the bundle file for the full list of certificate authorities and their certificates.
- GlobalSign Root CA
- net
- Baltimore CyberTrust
- Entrust Root Certification Authority
- Comodo AAA Services root
- QuoVadis Root
- Security Communication Root CA
- XRamp Global CA Root
- Go Daddy Class 2 CA
- Starfield Class 2 CA
- DigiCert Assured ID Root CA
- DigiCert Global Root CA
- DigiCert High Assurance EV Root CA
- SwissSign Gold CA - G2
- SwissSign Silver CA - G2
- SecureTrust CA
- Secure Global CA
- COMODO Certification Authority
- Network Solutions Certificate Authority
- COMODO ECC Certification Authority
- ePKI Root Certification Authority
- certSIGN ROOT CA
- Hongkong Post Root CA 1
- SecureSign RootCA11
- Microsec e-Szigno Root CA 2009
- GlobalSign Root CA - R3
- Autoridad de Certificacion Firmaprofesional CIF A62634068
- Starfield Root Certificate Authority - G2
- AffirmTrust Commercial
- TWCA Root Certification Authority
Download CA root certificates
Download the bundle of CA root certificates from curl.haxx.se. If it is not get downloaded automatically, just copy everything and save the copied content as cacert.pem in your local system. Then move this file to a proper location. Ex: xampp/php/extras/ssl.
Update php.ini file
To update php.ini file, open it and search for “curl.cainfo”. Set the file path of cacert.pem file as the value of the curl.cainfo variable. Make sure to put .txt at the end of the file path. Finally, uncomment the line that is having curl.cainfo variable.
Example:
curl.cainfo = “C:\xampp\php\extras\php\ssl\cacert.pem.txt
Note: If this does not work, remove .txt extension from the cacert.pem’s file path and try again.
FAQ
Q: What causes a curl error?
A: The cause is missing required CA root certificates from your CA root certificate bundle.
Q: How to ignore SSL certificate in curl?
A: In curl, you can make your connection insecure by specifying the -k option. But this is not recommended in production.
Comments
There are no comments yet.