User authentication and authorisation techniques
In the data security, organizations use a variety of user authentication and authorization techniques to safeguard sensitive data and valuable resources. For individuals navigating the complex organizational cybersecurity, terms such as LDAP (Lightweight Directory Access Protocol), AD (Active Directory), IDM (Identity Management), and others may seem like a technical jargon. This article unravel these concepts, providing a comprehensive understanding of each technique.
Different types of users in a system
In user authentication and authorization, understanding the various types of users within a system is important for implementing robust security measures. Each user role has a specific set of permissions and responsibilities, contributing to the overall structure of user management and access control. Let’s explore how these different user roles correlate with user authentication and authorization in a typical system.
At the top of user hierarchy is the Super Admin. This role holds paramount significance in the authentication and authorization landscape as it possesses the unrestricted authority to perform any operation within the system. From managing users to overseeing infrastructure, the Super Admin is the linchpin for maintaining system integrity and security.
Authentication mechanisms ensure that only authenticated individuals can assume this role, while authorization mechanisms strictly regulate the actions permissible to the Super Admin, safeguarding against unauthorized access.
Regular Users, constituting the majority of system inhabitants, have distinct capabilities centered around the usage, deployment, and management of applications. However, they are explicitly restricted from managing applications deployed by other users.
User authentication verifies the identity of individuals seeking access, and authorization mechanisms meticulously define the scope of their actions, preventing unauthorized interference with applications owned by their peers.
Moving on to administrative roles, the Tenant Admin assumes a pivotal position. Responsible for managing tenant users and overseeing applications and deployments within a specific tenant, the Tenant Admin’s role is closely tied to both user authentication and authorization.
Robust authentication ensures that only designated individuals can hold this administrative position, while stringent authorization mechanisms dictate the extent of their control over tenant-related resources.
The concept of a Tenant introduces a logical grouping of users sharing common objectives or collaborative efforts. In the context of user authentication, tenants represent distinct entities with their unique user pools. User authentication within a tenant ensures that individuals belong to the authenticated user pool of that particular tenant.
Moreover, tenants facilitate a hierarchical structure, allowing each tenant user to have a Tenant Admin. Authorization mechanisms define the specific permissions accorded to users within their respective tenants, fostering a secure and organized approach to collaborative projects or applications.
What is authentication and authorization?
Authentication and authorization are two fundamental components of any robust security framework.
Authentication is the initial step in the process, focusing on verifying and validating the identity of an entity, typically a user or system. The primary objective is to ascertain whether the claimed identity aligns with the actual identity of the entity seeking access.
In the digital world, this often involves presenting credentials such as usernames and passwords, biometric data, or cryptographic keys. The authentication process acts as a gatekeeper, allowing only authenticated entities to proceed further. Strong authentication mechanisms are essential for avoiding unauthorized access and safeguarding sensitive information.
On the other hand, authorization comes into play once the entity’s identity has been successfully authenticated. Authorization involves granting specific permissions and privileges to the authenticated entity, dictating what actions or resources the entity is allowed to access.
The level of access granted is contingent upon predefined rules and policies established by the system administrator or security protocols. Authorization mechanisms serve as the second line of defense, ensuring that authenticated entities operate within the confines of their designated roles and responsibilities.
What is RBAC?
RBAC stands for role-based access control. As the name suggests, it is an approach to control accessing data or systems to perform only granted operations based on role. For example, let’s take two roles super-admin and user.
Super-admin can perform any operation on a system including user and infrastructure management. But users can only use, deploy and manage applications. Users can’t manage applications deployed by other users. Admin can create roles, grant permissions to those roles, and assign roles to users.
Let’s take a typical role called editor. Admin creates the editor role, assigns permissions, “create posts, edit posts” and then assigns the role to a user in the organization. One role may have more than one permission. Also, one user may have more than one role.
What is an AD account?
An Active Directory (AD) account serves as a pivotal element in the Microsoft ecosystem, functioning as a centralized repository for user accounts, security groups, computers, and various network resources.
Unlike the conventional approach of dispersing user account information across individual computers and network components, AD consolidates this data into a unified and organized directory/database. This centralized structure streamlines account management and facilitates efficient access control within an organization’s network.
Administrators wield significant control and authority over AD accounts, wielding the ability to perform essential functions such as creating and deleting user accounts, as well as resetting passwords. The centralized nature of AD empowers administrators to manage user account data effortlessly.
Notably, this centralized capability proves advantageous in scenarios like password resets. When users need to reset their passwords, they can do so in one central location—the Active Directory. This eliminates the need for users to navigate through individual computers, enhancing user experience and administrative efficiency.
One of the critical advantages of AD lies in its integration with the Lightweight Directory Access Protocol (LDAP). AD’s directory service capabilities enable seamless integration with LDAP, a standardized protocol used for accessing and managing directory information services.
This integration enhances interoperability and extends the functionality of AD across diverse network environments.
In essence, an AD account is more than just a user credential; it represents a comprehensive approach to managing and organizing user accounts and associated network resources centrally.
The functionalities provided by AD not only simplify administrative tasks but also contribute to a secure and streamlined user experience within the Microsoft ecosystem.
What is LDAP and how does it work?
Lightweight Directory Access Protocol (LDAP) is a protocol designed for accessing and managing distributed directory information services in a network. Operating on a client-server model, LDAP facilitates communication between lightweight LDAP clients and directory servers.
The directory service, structured in a tree-like hierarchy, stores and organizes information in a manner that enables fast searching and browsing capabilities.
The fundamental concept of LDAP revolves around a hierarchical data model. In this model, information is organized into entries, each represented by a unique Distinguished Name (DN) within the directory tree.
Each entry comprises attributes, which hold specific pieces of information. LDAP supports a wide array of use cases, but in this context, the focus is on its role in user authentication within a networked environment.
For user authentication, LDAP serves as a crucial component in verifying and authorizing user identities. When a user attempts to access a network resource or system, the LDAP client initiates a query to the directory server to validate the user’s credentials.
The lightweight nature of the protocol ensures efficiency in this process, making LDAP particularly well-suited for scenarios where quick and reliable access to directory information is essential.
LDAP’s adaptability and simplicity contribute to its widespread adoption, especially in scenarios where directory services play a pivotal role. As a standardized protocol, LDAP promotes interoperability and facilitates seamless communication between various systems and applications, making it a cornerstone technology for user authentication and directory management in diverse network environments.
Here are some technical features of LDAP
- Not a database. But it uses databases (directory services such as AD) to store data.
- It runs over TCP/IP and can be accessed over port 389. SSL-enabled LDAP is abbreviated as LDAPS and can be accessed over port 636.
- A cross-platform protocol. That means LDAP can be run on any OS such as Linux, Windows, etc.
- LDAP doesn’t encrypt data by default and it can restrict resources such as individuals, and organizations to certain operations and data.
- LDAP database or LDAP directory (active directory or similar directory service) stores and retrieves data in a simple format and provides a well-structured set of records that is organized as a hierarchy by using schemas that define a set of rules to describe what kind of data is stored.
- The hierarchy of information stored in an LDAP database or LDAP directory is known as a directory information tree (DIT).
- Read more about LDAP on openldap.org.
What is IDM authentication?
Identity Management (IDM) is a comprehensive system comprising policies and technologies designed to oversee and verify user identities within an organization.
The primary objective of IDM is to ensure that individuals or groups of users possess the appropriate permissions to execute specific operations on organizational resources. Beyond mere user authentication, IDM encompasses a broader scope, extending its influence over the entire identity lifecycle, from creation to termination.
It also includes the strategic management of access permissions, ensuring that users are granted appropriate levels of access to hardware, applications, and other resources within the organization. This proactive approach to access management enhances security by aligning permissions with organizational roles and responsibilities.
IDM-enabled hardware and applications become integral components of the organization’s security infrastructure. By leveraging IDM techniques, organizations can implement robust access control mechanisms, monitor user activities, and streamline the provisioning and deprovisioning of user accounts.
The goal is to establish a centralized and efficient system that not only authenticates users but also governs their access privileges throughout their interaction with organizational resources.
Here are some technical features of DIM authentication
-
User Registration
The IDM process typically begins with user registration. When a new user joins an organization or system, their identity is recorded within the IDM system. This involves collecting essential information such as username, password, and additional attributes based on organizational requirements. -
Identity Verification
During the registration process, the user’s identity is verified using various authentication methods. This may include traditional username-password authentication, multi-factor authentication (MFA), biometric verification, or other secure means. The goal is to establish a strong assurance of the user’s identity. -
Access Request and Authorization
Once registered and verified, users can request access to specific resources or services within the organization. These access requests are subject to an authorization process, where the IDM system evaluates the user’s permissions based on predefined policies and roles. -
Role-Based Access Control (RBAC)
IDM often employs a role-based access control (RBAC) model. Users are assigned roles based on their job responsibilities, and these roles determine the level of access they have. RBAC streamlines access management by associating permissions with specific job functions. -
Single Sign-On (SSO)
IDM systems frequently incorporate Single Sign-On (SSO) capabilities. SSO allows users to log in once and gain access to multiple systems or applications without the need to reauthenticate for each one. This enhances user experience and reduces the burden of managing multiple credentials. -
Identity Federation
In scenarios involving multiple systems or organizations, identity federation ensures seamless authentication across different domains. Federation allows users to access resources in partner organizations without the need for separate credentials, promoting interoperability. -
Continuous Monitoring and Adaptive Authentication
IDM systems often include continuous monitoring features. Behavioral analytics and other risk-based assessments may trigger adaptive authentication measures. For example, suspicious activity might prompt the system to request additional verification steps. -
De-provisioning and Lifecycle Management
When a user’s role changes, or they leave the organization, IDM systems facilitate efficient de-provisioning. This involves revoking access rights, disabling accounts, and managing the entire lifecycle of user identities. -
Audit Trails and Reporting
Comprehensive audit trails are maintained by IDM systems, documenting user activities, access events, and authentication attempts. These logs contribute to security and compliance efforts, allowing organizations to review and analyze user interactions.
What are Service accounts?
In the realm of identity and access management, service accounts emerge as a specialized category designed for non-human entities within an organizational ecosystem. Unlike user accounts associated with human individuals, service accounts cater to applications, scripts, robots, or virtual machines (VMs) seeking programmatic access to various systems or services. These accounts play a pivotal role in enhancing automation, efficiency, and security across diverse IT environments.
Authentication and Authorization:
Service accounts primarily serve as a means of authentication and authorization for non-human users. They enable automated processes and applications to interact with other components within the system, performing tasks and operations granted to them. Authentication involves proving the identity of the service account, while authorization dictates the specific actions or operations it is permitted to undertake.
Non-Human Entities:
The nature of service accounts aligns with the idea that not all users in a system are human. Many processes and tasks can be efficiently handled by automated entities, and service accounts provide the mechanism for these non-human entities to establish their identity and access permissions. This is particularly valuable in scenarios where continuous, scripted, or background operations are required.
Automation and Script Execution:
Developers and IT engineers leverage service accounts to automate the execution of services, applications, or scripts. By assigning a service account to a specific application or script, developers empower these entities to authenticate themselves and carry out predefined operations without manual intervention. This automation streamlines workflows, reduces manual errors, and ensures consistent execution.
Granular Access Control:
Service accounts contribute to a granular approach to access control. Instead of relying on a shared, generic account, each application or script can have its dedicated service account with tailored permissions. This enhances security by limiting access to only the resources necessary for the designated functionality, adhering to the principle of least privilege.
Secure Communication:
Service accounts often utilize secure methods of communication, such as API keys or OAuth tokens, to establish trust and facilitate secure interactions. This ensures that non-human entities can securely communicate and collaborate within the system without compromising sensitive information.
Lifecycle Management:
Just like user accounts, service accounts undergo lifecycle management processes. This includes creation, modification, and, when necessary, deactivation or removal. Proper management of service accounts ensures that they align with the evolving requirements of the applications and scripts they represent.
What is Vault?
Vault serves as a centralized and secure repository for storing and accessing credentials crucial for authentication or authorization to various systems. Credentials encompass a wide range of sensitive information, including passwords, API keys, tokens, and certificates. The centralized nature of Vault offers several advantages for administrators, making credential management more efficient.
One notable benefit is the Secret Encryption feature, ensuring that credentials remain concealed and inaccessible to unauthorized individuals. Vault encrypts all stored secrets, employing robust security measures to safeguard sensitive information. Additionally, the centralized structure facilitates streamlined administration, allowing administrators to easily manage all credentials from a single location.
Vault incorporates a comprehensive set of features that contribute to its effectiveness. Auditing activities play a major role as Vault logs all interactions, enabling administrators to monitor who interacts with the vault and the actions they perform. This auditing capability enhances transparency and accountability in credential management.
Moreover, Vault enforces Access Control, ensuring that credentials cannot be accessed without proper authentication. This security measure adds an extra layer of protection, mitigating the risk of unauthorized access.
The architecture of Vault follows a client-server model, providing flexibility for users and applications to interact with it through JSON over HTTP (REST) or the vault command-line interface (CLI). The core component of Vault plays a crucial role in processing requests and managing the secure storage of encrypted secrets.
The vault kv get command is a key feature that allows users to retrieve and display decrypted values from the vault, facilitating efficient access to stored credentials.
The default secret engine in Vault is kv, situated at the path “secret,” where kv stands for key-value. Users have the flexibility to add more secret engines based on specific requirements.
The availability of various secret engines in the market offers diverse functionalities, each catering to different use cases. A sample payload is provided as an example for storing a new secret in the vault, showcasing the simplicity and effectiveness of the process.
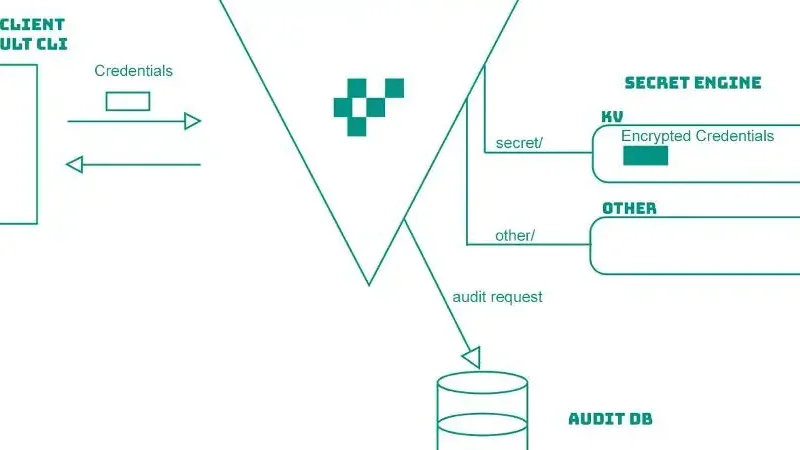 Vault Architecture
Vault Architecture
In conclusion, Vault stands as a robust solution for secure credential management, offering a centralized, encrypted, and auditable platform. Its flexibility in supporting different secret engines makes it adaptable to diverse industry needs, providing a comprehensive and scalable approach to credential security.
Vault is a centralized mechanism to store and access credentials securely. Credentials are anything that might grant you authentication or authorization to a system. For example, passwords, API keys, tokens, or certificates.
- Read more about Vault on vaultproject.io.
Conclusion
In conclusion, safeguarding resource data is paramount in the contemporary digital landscape, where the significance of protecting sensitive information against unauthorized access cannot be overstated. In addressing this imperative, various techniques such as LDAP, AD, IDM, and Vault play crucial roles.
LDAP and AD provide robust directory services, while IDM offers comprehensive identity management solutions. Vault, on the other hand, emerges as a centralized mechanism for securely storing and accessing critical credentials.
Employing these techniques collectively fortifies the defenses against unauthorized access, ensuring the integrity and confidentiality of resource data in an ever-evolving and interconnected world.
FAQ
Q: What is the difference between a service account and a user account?
A:Usually, service accounts are used to authenticate non-user service resources. For example, if you want back up your website to google drive automatically without user intervention, it can be done by a service account. User accounts are used by real users. Just like you. For example, your Facebook account.
Q: How to create Service Account in Google Cloud Console?
A: Check out this documentation to create Service Account in Google Cloud
Q: Can LDAP be integrated with AD?
A:Yes. AD is a directory service which supports LDAP.
Q: What is a directory service?
A:Directory service is a database that is specifically designed for fast searching and browsing. But not restricted to those two operations. It supports update and lockup operations as well.
Comments
There are no comments yet.